20 TOP VOICES OF CYBER SECURITY AND INFORMATION SECURITY FOR MARCH 2018 BY JAN BARBOSA

Cyber Security and Information Security deal with the ever-increasing problem of how to maintain your information secure. While both terms deal with the security of information, they differ on how broad their responsibility reach is.
Cyber Security deals with data that is stored in electronic form.
Wikipedia defines Cyber Security as: " The protection of computer systems from the theft and damage to their hardware, software or information, as well as from disruption or misdirection of the services they provide.
Cybersecurity includes controlling physical access to the hardware, as well as protecting against the harm that may come via network access, data, and code injection. Also, due to malpractice by operators, whether intentional or accidental, ITsecurity is susceptible to being tricked into deviating from secure procedures through various methods."
Information Security on the other hand also deals with security not stored in electronic format. Think of information locked on cabinets, desk drawers or even thrown in the garbage containers. It might be manuals, maps, job resumes, health records and microfiche cards.
Wikipedia defines Cyber Security as: "The practice of preventing unauthorized access, use, disclosure, disruption, modification, inspection, recording or destruction of information. It is a general term that can be used regardless of the form the data may take (e.g., electronic, physical).Information security's primary focus is the balanced protection of the confidentiality, integrity, and availability of data (also known as the CIA triad) while maintaining a focus on efficient policy implementation, all without hampering organization productivity.This is largely achieved through a multi-step risk management process that identifies assets, threat sources, vulnerabilities, potential impacts, and possible controls, followed by an assessment of the effectiveness of the risk management plan.
Cyber Security and Information Security both deal in protecting data that in the wrong hands could cause havoc in our lives. Identity theft causes billions of dollars to consumers and banks, Ransomware has wiped out terabytes of critical data to those unwilling to yield to hackers demands. Both Cyber Security and Information Security are one of our most important lines of defense against these ever-increasing attacks.
These are the top 20 voices of Cyber Security and Information Security for the month of March 2018 as gathered by @klout.
CYBER SECURITY:
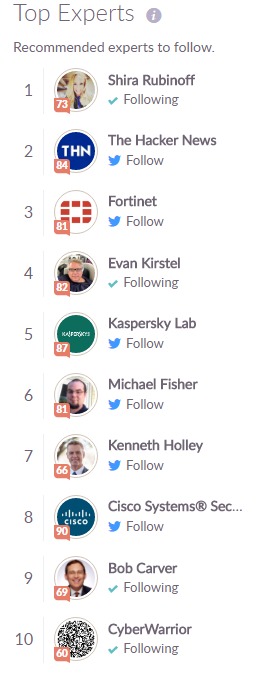
INFORMATION SECURITY:
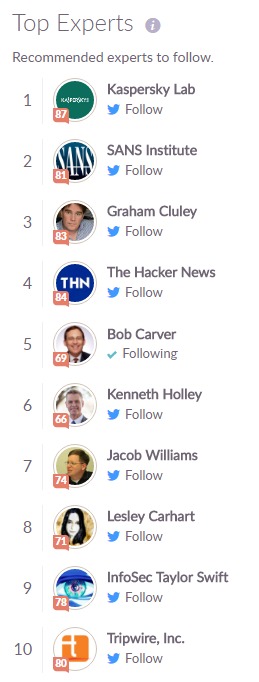
Congratulations and thanks to all the great minds sharing their knowledge of Cyber Security and Information Security.

As a technology advocate, he strongly promotes and participates in areas such as Artificial Intelligence, Augmented / Virtual Reality, and Cyber Security.
All articles are initially published in beBEE.com using the superb beBEE Producer tool.
Feel free to Follow Jan Barbosa on Twitter, LinkedIn or beBEE.com
Artículos de Jan 🐝 Barbosa
Ver blog
According to the United States Department of Labor, employment of information security analysts is p ...

Nepotism is a type of favoritism shown towards family members in the workplace. It occurs when those ...

There is a reason why corporations (and hackers) are trying to gather as much of your data as possib ...
Profesionales relacionados
Puede que te interesen estos puestos de trabajo
-

Asociado De Almacén
Encontrado en: Buscojobs PR C2 - hace 5 días
Ibp, Llc Arroyo, Puerto RicoEmpresa de fabricación ofrecerá un puesto de asociado de almacén a tiempo completo. De lunes a viernes, 40 horas semanales, de 8 a. m. a 4 p. m., pero flexible. Debe ser confiable y puntual.Requisitos:El trabajo incluye envío, recepción, oficina, cumplimiento de pedidos y logísti ...
-
Account Executive
Encontrado en: Talent PR C2 - hace 2 días
Upturn Co. Guaynabo, Puerto RicoDescripcin general del puesto: · Responsable de brindar apoyo enventas y mercadeo a productores de seguros de Salud y Beneficios yPropiedad y Contingencia y Clientes en el desarrollo de relacionesde negocio con clientes nuevos y existentes. Identifica lasnecesidades de estos y of ...
-

Administrative Assistant
Encontrado en: Buscojobs PR C2 - hace 13 horas
Adecco Guánica, Puerto RicoThe incumbent will be responsible for assisting in administrative office activities related to Human Resources, Procurement, QMS, Safety, Regulatory and Stewardship compliance, record keeping and other programs of the Guanica Puerto Rico Soybeans Breeding / T-I Station for R&D. P ...

Comentarios
CityVP Manjit
hace 6 años #2
This is something I want to come back to and explore, especially now as I spend an outrageous amount of time with media and club development for the campus toastmasters club I am associated with - that includes some 200+ tweets this month to put some meat on the bone for just one Twitter account at @sbotoastmasters - so will be glad when I can digest your links when I have uninterrupted time and space to think about this particular sector of technology.
Jan 🐝 Barbosa
hace 6 años #1